Malicious Website Alert!!!
Or not (as the case may be). Let’s explore shall we.
On the 21st of July, Anglican Mainstream sent out an email that said the following:
A new article was posted on Anglican Mainstream today that linked to a website which, although appearing legitimate, was in fact classified by my security system as a ‘known attack website’.
In layman’s terms this means that the website contained a malicious program design to infect the PC when visiting. These ‘attack’ programs are designed to install programs that steal private information, use your computer to attack others, or damage your system. Please note that these programs are also used for keylogging and spying purposes.
The website in question was the Inclusive Church site, though that site was explicitly not mentioned in the email.
Colin Coward of Changing Attitude though wrote a blog post where he linked the email to a rant about exorcising demons of homosexuality (demons, demonisation – see what he did there?). In it he wrote:
Meanwhile, I learnt from Giles Goddard that Anglican Mainstream has sent an email to members of General Synod and others to tell them that the Inclusive Church web address is an “attack websiteâ€.
The person responsible (or irresponsible) for the email is Canon Chris Sugden, member of General Synod and Executive Secretary of Anglican Mainstream International.
Chris was responding to an alert from an Anglican Mainstream supporter and tech specialist. In he email he says he really appreciated the supporter taking the time to write “and fill us in on how to respond to some disconcerting technological challenges. The link his computer found to be a known attack website was that of Inclusive Church.â€
The Mainstream supporter says his computer security system classified a link to the Inclusive Church website in a news item posted today by Mainstream as a ‘known attack website’. He said this meant that the website contained a malicious program designed to infect the PC when visiting. ‘Attack’ programs are designed to install programs that steal private information, use your computer to attack others, or for spying purposes.
Actually, that last sentence is quite a good summary of the problems some sites have. So what’s going on at the Inclusive Church website then?
Well, were you to stroll over to www.inclusivechurch.net using Firefox, this is what would greet you.
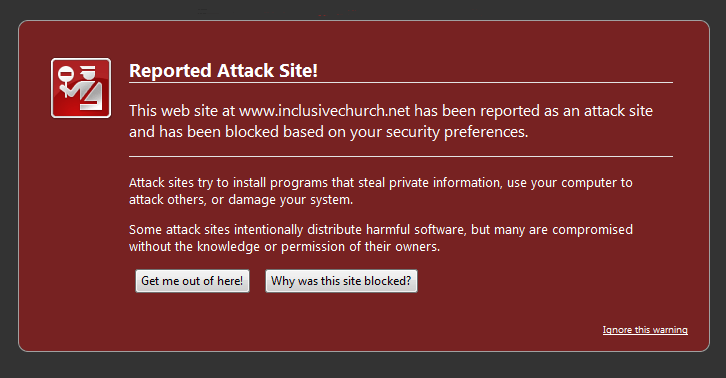
That’s kinda scary isn’t it? Click on the “Why was this site blocked?” button and the following fascinating information is unveiled.
Of the 2 pages that we tested on the site over the past 90 days, 1 page(s) resulted in malicious software being downloaded and installed without user consent. The last time that Google visited this site was on 2009-07-20, and the last time that suspicious content was found on this site was on 2009-07-20.
Malicious software is hosted on 2 domain(s), including d99q.cn/, onosill.cn/.
1 domain(s) appear to be functioning as intermediaries for distributing malware to visitors of this site, including d99q.cn/.
This site was hosted on 1 network(s) including AS29017 (GYRON).
Sounds serious, but in fact the trojan that Google is reporting is a fairly harmless piece of malware written years ago. So what was it doing on the Inclusive Church website? Well, the answer is that it wasn’t really. Here’s what’s most likely gone on.
- The inclusivechurch.net domain hasn’t been used for a while. Inclusive Church switched to using inclusivechurch2.net a while ago (as far back as the end of November 2007).
- The inclusivechurch.net domain was repointed to inclusivechurch2.net. This means that if you typed www.inclusivechurch.net into your browser it would automatically go to www.inclusivechurch2.net
- At some point along the line, the IP address that is handling the inclusivechurch.net DNS has been associated with another site that has a malicious link on it. This is not uncommon, because unless you host on your own server your site will most likely share an IP address with other sites. On top of this, the server handling your domain details (DNS) will handle the details of hundreds (thousands) of other sites (as the one handling inclusivechurch.net is – see here for a list of name servers on the same IP address and other domains).
- Google regularly checks for malware as it spiders through the web and for some reason on the 20th of July (or earlier) registered a very old Trojan on www.inclusivechurch.net. This could have been for any number of reasons:
- The domain was parked and the parking site had a malicious link
- The spider got confused as it explored the IP address that the domain www.inclusivechurch.net uses for DNS purposes.
- The redirect was hard coded as an HTML page, which was itself compromised and malicious code inserted.
- Something else, but absolutely nothing to do with the peeps at Inclusive Church
The one thing it can’t be is that the Inclusive Chuch website itself hosted something malicious, because if that were so then the domain www.inclusivechurch2.net would also have been flagged. It was therefore incorrect to say that “the website was an attack website”. This is simply untrue. The domain www.inclusivechurch.net has been flagged, but the actual website itself is fine.
As of yesterday afternoon www.inclusivechurch.net (the domain, not the website) has been taken offline – not even parked. Even attempts to ping it are coming back blank. Obviously Richard Thomas (or someone else, but the website is registered to him) has decided to pull the plug until he works out what’s going on. My suggestion to fix the problem? Given that the domain is registered with 123-reg, it should be no problem to use their domain control panel to simply redirect to the new domain. That should solve the problem and is much better solution then hard coding in HTML the redirect (which is what I suspect they did previously, hence the problem).
Oh, and they could do worse then to junk their 8 year old content management system.
What’s the moral of the story? Your friendly neighbourhood techy guy may not actually be as clued up as he claims. Always best to investigate what’s actually going on before jumping to the wrong conclusions.
Thanks Peter – very informative.
Apart from the technicalities, what have we learned? That people are inclined to believe the worst about those they oppose, I guess. Shouldn’t be so among Christians, though.
I think we’ve learnt that people on both sides are quick to jump to assumptions. Someone at Mainstream jumped to an assumption about the Inclusive Church website, and in return, Colin Coward jumped to an assumption about the reasons for the email (which to be fair to Mainstream was simply to apologise for including a link that might lead to a trojan being downloaded).
I think Anglican Mainstream and Chris Sugden were right to send out the email alert as better safe than sorry.
Unfair however to give the impression that a website has done something malicious on purpose, when they themselves may also be the victim of an attack.
Max